Migration Chaos or Migration Clarity? The Choice Is Yours.
Blog Migration Chaos or Migration Clarity? The Choice Is Yours. Learn how ZENmig transforms complex moves into predictable, risk-free transitions.
With cyber threats constantly evolving and old access controls not cutting it anymore, how can you strengthen your defenses and keep sensitive data safe?
Let’s face it! Effective cybersecurity starts with Privileged user risk assessment. Making sure the right people have access at the right times is crucial, especially as digital transformation speeds up. If you’re like most, you’re probably finding it more and more challenging to protect your company from modern threats. Implementing smart privilege controls is essential for an identity-first strategy.
Ignoring Privileged user risk access (PAM) isn’t just risky; it’s a recipe for disaster, think data breaches, lost customer trust, and hefty fines. Imagine an employee with too much access could easily sabotage or mess with your data.
But Privileged user risk assessment is more than just authentication and authorization; it’s about visibility, governance, and compliance. For instance, in healthcare, Privileged user risk assessment is vital for protecting patient data and staying compliant with HIPAA regulations. Robust user risk access management practices are key to reducing risks and maintaining trust.
Enter zRacs by ZENfra—a cutting edge solution tailored to meet the complex security needs of today’s businesses.
Protect Your Data Today
Learn how zRacs can enhance your cybersecurity.
Businesses in all sectors face increasingly sophisticated cyber threats. Traditional security measures just can’t keep up, leaving you exposed to breaches and compliance risks. Static controls and a lack of insight into access patterns only make things worse. So, how do you effectively tackle these vulnerabilities?
Privileged user risk assessment helps you know exactly who’s accessing your data and systems, why they’re doing it, and what actions they’re taking. Without it, enforcing security policies and meeting compliance requirements is impossible. Plus, you can’t hold users and partners accountable for their actions.
This is especially critical now, with digital transformation, cloud migration, remote work, and mobile devices all adding layers of complexity. These trends have expanded the attack surface and increased the risk of identity compromise.
You’re also grappling with a bunch of identity-related challenges—identity sprawl, orphaned accounts, privileged access abuse, credential theft, password reuse, shadow IT, and identity fraud. Each of these adds to the complexity and potential risks.
Stay Ahead of Cyber Threats
Find out how zRacs can keep your data safe.
zRES uses AI to detect vulnerabilities and predict security incidents by analyzing patterns. It alerts your team to risks like improper permissions or insider threats, enabling preemptive action.
During ransomware attacks, zRES identifies systems with secure backups and their locations for swift recovery, minimizing downtime. It ensures optimal backup strategies by analyzing patterns.
zRES facilitates smooth recovery by pinpointing recent recovery points and analyzing data loss during incidents. It identifies the best backup for retrieval, minimizing downtime and data loss.
zRES manages vulnerabilities and patches, controlling user permissions effectively. It simplifies backup and recovery processes, reducing costs and manpower requirements.
zRES ensures compliance with industry standards and regulations, protecting against penalties and reputational damage. It keeps systems updated to maintain regulatory adherence and security.
zRES provides insights into storage utilization to prevent resource wastage and optimize performance. It identifies systems nearing capacity and recommends upgrades for operational efficiency.
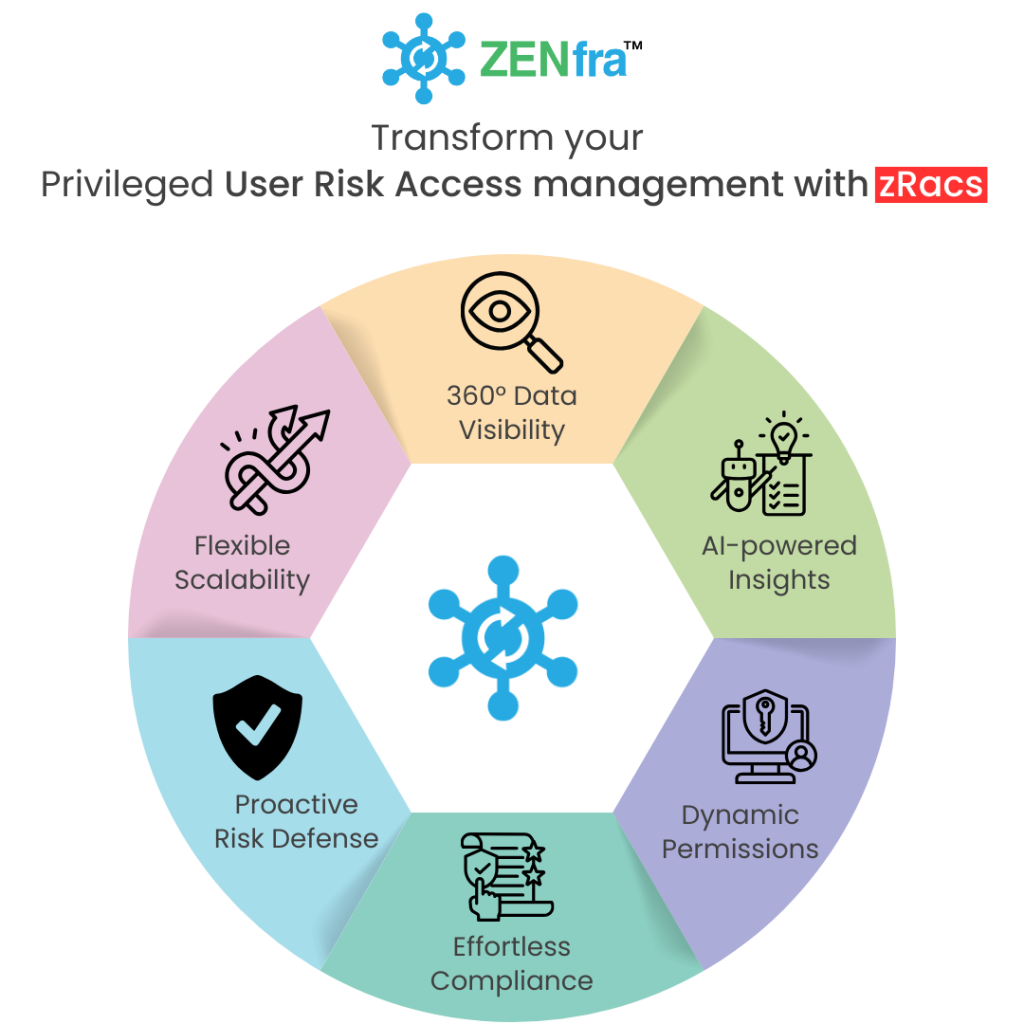
Contact us for a personalized demo and discover how zRacs can empower your organization with robust User Privileged Access Management.
Ready to elevate your security strategy?
Discover how zRacs can transform your Privileged User Risk Access Management and protect your organization from evolving cyber threats. Request a personalized demo today!

Migration Chaos or Migration Clarity? The Choice Is Yours.
Blog Migration Chaos or Migration Clarity? The Choice Is Yours. Learn how ZENmig transforms complex moves into predictable, risk-free transitions.

Stop Reacting. Start Leading: Transform IT Chaos into Growth with ZENfra Asset Lifecycle Management
Blog Stop Reacting. Start Leading: Transform IT Chaos into Growth with ZENfra Asset Lifecycle Management Its biggest threat isn’t always

How Fortune 500s Gain Real ROI and Compliance With AI-Driven Asset Lifecycle Management
Blog How Fortune 500s Gain Real ROI and Compliance With AI-Driven Asset Lifecycle Management AI in Action: Delivering Tangible ROI
5000 Quorum Drive
| Suite 710 | Dallas, TX 75254