
From hoping data survives to proving recovery works – cyber resilience is being redefined.
Blog Migration Chaos or Migration Clarity? The Choice Is Yours. Learn how ZENmig transforms complex moves into predictable, risk-free transitions.
Imagine your organization buzzing with activity while unchecked accounts and forgotten passwords quietly lie in wait, poised to cause trouble. Cyber threats can feel like a game of chance one wrong move and the consequences can be severe. With data breaches dominating headlines, many organizations grapple with common challenges, such as excessive user access, weak password practices, and a lack of visibility into who is accessing sensitive information. These vulnerabilities create an environment ripe for exploitation, where dormant accounts can serve as secret pathways for attackers. The risks become alarmingly clear when considering a scenario where a former employee retains access to critical data, opening the door to potential breaches.
To combat these escalating threats, organizations must take proactive steps to manage access and protect their valuable information. Implementing robust security measures is essential to effectively mitigate risks and maintain control over sensitive data. By limiting user privileges and improving overall access visibility, businesses can create a more secure environment, reinforcing trust among employees and customers alike.
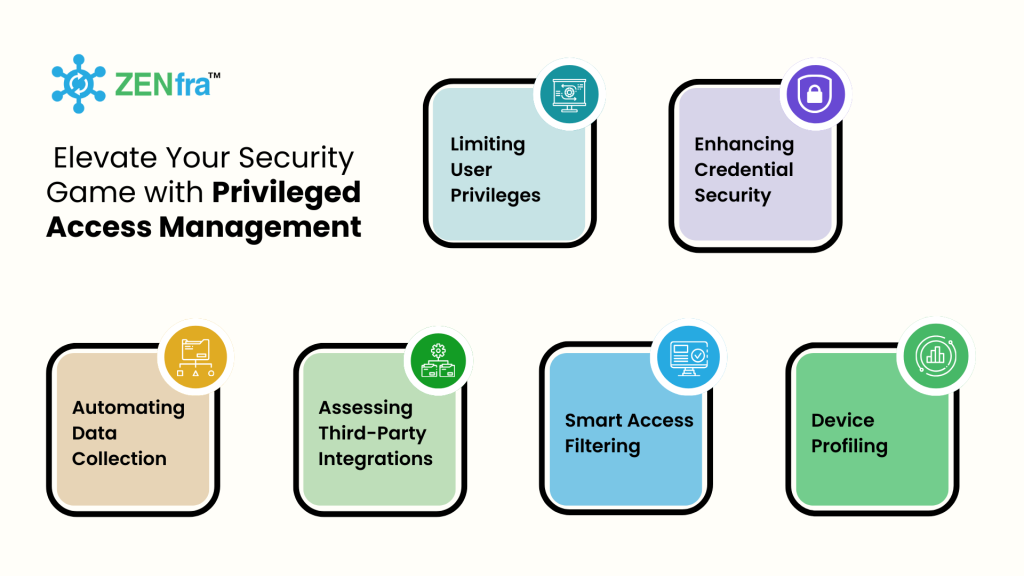
By implementing ZENfra’s PAM solutions, organizations can significantly elevate their security posture while enhancing operational efficiency. Here’s how ZENfra’s PAM solutions offer tangible improvements by effectively addressing prevalent security risks:
For a global insurance provider handling highly sensitive customer data, ZENfra’s Privileged Access Management (PAM) has become a core component in transforming their security framework. Integrating seamlessly with the provider’s existing systems via ZENCollector, PAM automates data collection and delivers immediate alerts on unauthorized access attempts, enhancing proactive security measures. By leveraging advanced data analysis and behavior pattern recognition, PAM identifies irregular access patterns, leading to a 40% reduction in security incidents and ensuring that users access only what they need. This boosts operational efficiency by 30%.
Additionally, PAM actively monitors permission changes and password updates to detect unusual activity, while providing tailored security recommendations. Through the evaluation of third-party integrations and device profiling, PAM further reduces operational vulnerabilities by 25%, protecting against compromised devices and safeguarding critical data. This solution not only mitigates potential security risks but also optimizes efficiency, saving millions in potential breach costs and enabling the provider’s teams to focus on core responsibilities.
Ready to lead the charge?
Contact us today to discover how ZENfra’s AI-powered solutions can transform your projects and propel your business forward.
ZENfra’s AI-powered solutions can help you predict, secure, and streamline your cloud initiatives. Ready to take the lead? Let’s talk!

From hoping data survives to proving recovery works – cyber resilience is being redefined.
Blog Migration Chaos or Migration Clarity? The Choice Is Yours. Learn how ZENmig transforms complex moves into predictable, risk-free transitions.

Smarter optimization. Measurable gains. Zero compromise
Blog Migration Chaos or Migration Clarity? The Choice Is Yours. Learn how ZENmig transforms complex moves into predictable, risk-free transitions.
Migration Chaos or Migration Clarity? The Choice Is Yours.
Blog Migration Chaos or Migration Clarity? The Choice Is Yours. Learn how ZENmig transforms complex moves into predictable, risk-free transitions.
5000 Quorum Drive
| Suite 710 | Dallas, TX 75254